
In-house lawyers can be the fence at the top of the cyber cliff, creating procedures to prevent the worst effects of a cyberattack and responding quickly and effectively when (not if) a cyberattack occurs.
Given how quickly cybersecurity has risen from being a line-item on the IT department’s annual budget to top of the list for most companies, in-house lawyers are now a critical gear in the machinery protecting a firm’s digital assets, client data and balance sheet.
General counsel must lead the charge in encouraging the C-suite to create, implement and test a robust cybersecurity incident response (IR) plan. The future success of their company could depend on it.
Just how much of a problem are cyberattacks and breaches in 2021?
US-based cybersecurity provider FireEye said in its M-Trends 2021 report that the Asia Pacific (APAC) region is the “most-targeted” region in the world for ransomware.
Ransomware is a form of malware that encrypts a victim’s computer files. The attacker then demands a ransom to restore access to the data. Users are shown instructions for how to pay a fee to get the decryption key.
FireEye’s report said on average, APAC organizations are attacked by ransomware roughly 51 times per week in 2021.
But it’s not just ransomware that is rising. Between May 2020 and May 2021, recorded instances of all types of cyberattacks on APAC-based companies rose 168%. And in just one month – April-May of this year – the entire region saw a whopping 58% increase in cyberattacks, year-on-year.
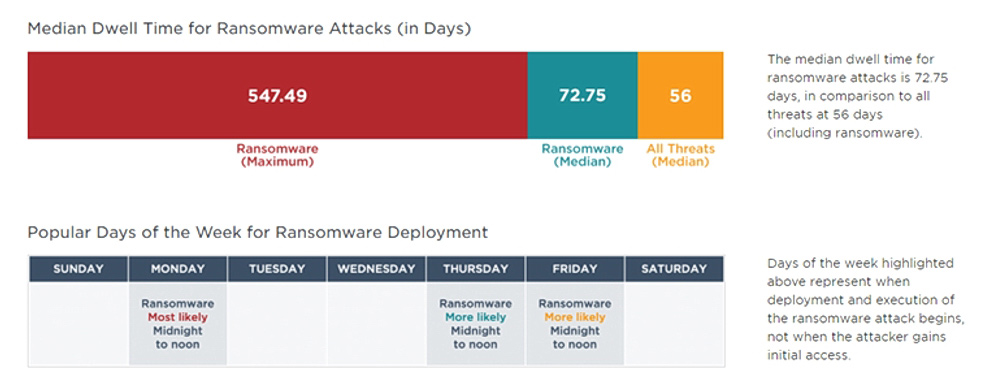
Image: Ransomware on the rise. ‘Dwell time’ indicates the time an attacker or malware variant sits on a computer system before it is activated or detected (credit: FireEye)
Unfortunately, the preparedness of APAC companies is not keeping pace with the rising cybercrime. Indeed, it may even be slipping further behind.
A study earlier this year by British security firm Sophos called The Future of Cybersecurity in Asia Pacific and Japan found 54% of Asia Pacific (APAC) companies had not updated their cybersecurity strategies at all in the last 12 months – despite the Covid-19 pandemic which forced millions of employees to work remotely.
“We asked organizations if they had a cybersecurity team in place that could detect, investigate and respond to threats. In 2019, 50% of organizations answered ‘no’, in 2021 that increased to 52%,” the study said.
Ransomware and ‘Double Extortion’
RPC partner Jonathan Crompton said while Covid-19 popularized the term “work from home,” the sheer number of these cyberattacks in 2021 will make “ransomware” and “double extortion” the cybersecurity buzzwords of 2021.
“Ransomware attacks have significantly increased as a proportion of all cyber incidents on which we are advising. We are also regularly seeing threat actors adopting the ‘double extortion’ technique by extracting personal data before triggering a ransomware encryption.
“It often comes with a threat that if payment isn’t made, the data will be published. Threats like this are designed to increase the chances of a victim company paying a ransom even if it has restored its systems. One group has even begun publishing the fact of a successful attack while negotiating the ransom payment to increase pressure on the company,” he said.
IronNet’s 2021 Cybersecurity Impact Report said APAC’s impressive economic growth means the region will continue to offer many juicy, high-value targets in a low-security environment for many years until companies realize the danger they are in and take action to defend themselves.
“Rapid digital transformation has expanded APAC cyberattack surface and there remains a disproportionately low level of investment in cybersecurity and risk management strategies by many organizations,” IronNet’s report said.
All this might seem daunting for in-house legal teams. However, a lot can be done – quickly and efficiently – by general counsel to mitigate the major vulnerabilities in their company’s computer systems.
After all, the in-house legal team is often the first phone call (after the IT department) that a CEO will make during a cyber incident to figure out what happened. So, they better have a plan.
Incident response
Some of this work has already begun in many companies.
In-house legal teams are often consulted to create data policies, business continuity plans, insurance options or by inserting appropriate clauses in contracts to protect a company’s interests.
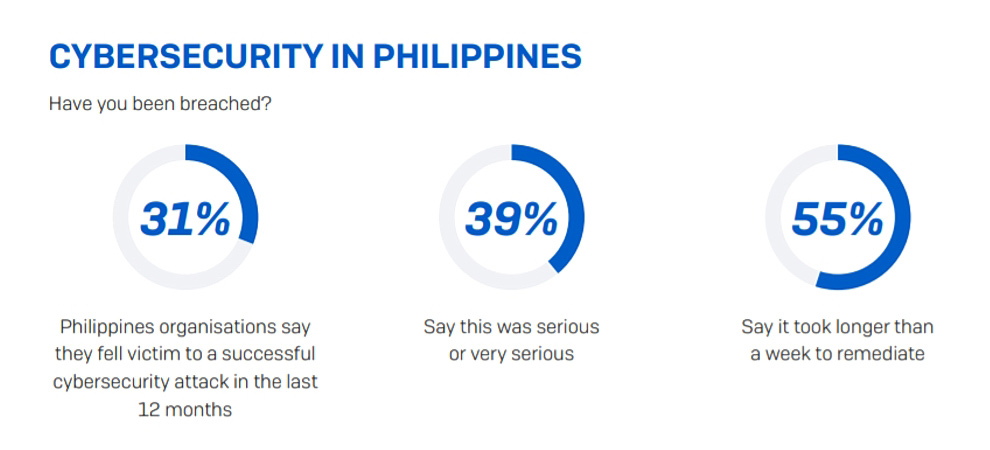
Image: Philippines struggling to cope with cyberattacks (credit: Sophos)
The problem facing in-house legal teams is that there can be a breakdown in process when a well-thought-out response plan is dusted off and executed in the crisis situation of a cyberattack. On top of that, many legal teams are still stuck using manual, ad hoc processes and out-of-date information which hurts their ability to make critical decisions during a breach.
One example of a recent cyber incident shows the importance of including general counsel in all conversations about security – ideally long before an incident arises.
The incident described below occurred at a major asset management company. A legal counsel for the company told IHC about the breach on condition of anonymity.
“Our firm identified a potential unauthorized access of an employees’ Outlook account (which our firm locked upon identification of the unauthorized access).
“Upon discovery, we took immediate action to remediate the situation and the unauthorized access to the employee’s account by this third party was terminated. We also engaged technical experts, including a cyber incident response manager and an independent leading global provider of risk solutions to thoroughly investigate the matter.
“The expert concluded the breach was limited to one email account and that the actions of the unauthorized actor were motivated by financial fraud and not theft or exfiltration of personal data,” the legal counsel said.
The counsel added that the incident could have been much worse if the company did not have in place appropriate policies and procedures to address cyberattacks quickly and if the key staff didn’t follow those steps.
Everyone did what they were supposed to do because they had the appropriate training, drills and assistance when those were all needed – before the cyberattack took place.
In-House Counsel at the Core
Crompton said in-house lawyers must be at the core of building a good crisis response plan by ensuring that data governance and security are regularly on the board’s agenda as a standing item.
“Preparation is key to post-breach response. It is much better to over-prepare than under-prepare,” he said.
Crompton added that a full cybersecurity and data governance plan must involve all areas of the business, including IT (infrastructure and security), finance and risk (insurance), communications (messaging) and the business.
Having access to good cyber insurance is also a great way to protect against the potentially significant costs of third-party service providers investigating and responding to a cyberattack.
Speaking on condition of anonymity, a general manager of legal and risk management at a multinational retail and supply chain group said instead of just focusing on the law, in-house counsels should know the operations side of the company as well, have a decent level of technical IT knowledge and, more importantly, be good communicators.
“Be quick, be transparent, be determined. Have specialists ready to call in an emergency. A business continuity plan (BCP) will avoid panic and we strongly advise having the BCP tested on a regular basis.
“But, the most challenging part of a plan is always the execution and the follow through,” the general manager said.
It’s not necessary for general counsels to have all the same technical information as an IT specialist, but they should have a basic understanding of all terms. They also need to be aware that cyberattacks can occur suddenly and can escalate rapidly.
Also, a general counsel should build a network of in-house and external lawyers to share how they handled cyber breaches and learn some tricks. This can be done through outside counsel if needed. Having these connections can relieve significant uncertainty (and therefore pressure) on an in-house team when a crisis happens, Crompton said.
Dealing with Ransomware
It seems above all other types of cyberattacks, ransomware is likely to be the type to hit most companies, at least over the next few years.
According to Steve Ledzian, CTO and Vice President, APAC of FireEye ransomware is “spiraling out of control” in the Asia Pacific.
Unfortunately, Ledzian says it can take an average of 76 days for organizations in the region to notice and respond to these kinds of intrusions, falling behind EMEA (Europe, Middle East, Africa) which averages 66 days and the Americas, averaging just 17 days.
“In many cases the attacker’s work is done well before the victim even knows something is wrong,” Ledzian said.
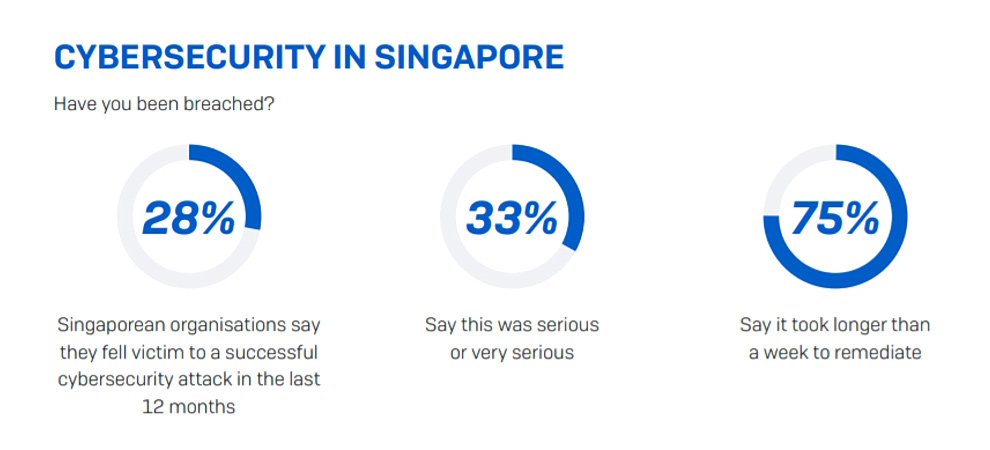
Image: Singapore-based companies say it can take a long time to recover from cyberattacks (credit: Sophos)
So, what can be done if a company’s computer systems are locked by ransomware?
Firstly, it may be possible to purge the locked systems, restore backed-up versions of the data and keep going as if nothing happened. After all, many large companies have the discipline to store multiple copies of their data so they can pivot to new machines easily without needing to pay the criminals a ransom to release it. It also pays to keep a hard copy of the response plan in case none of the computers are accessible during an attack.
But for others – smaller firms or larger companies caught off-guard – the only realistic option to recover the data or prevent further leakage is to attempt to pay the criminals. There is no guarantee the data will be unlocked (some criminals lock the data but don’t have the unlock codes themselves, while others will simply refuse to unlock the data even if they get a ransom).
If a company suffering a ransomware attack does choose to negotiate with the criminals, there are a few things to consider first, said RPC’s Crompton.
RPC has advised several companies that chose to pay a ransom. Crompton said these experiences show the benefit of using a cyber ransom negotiator if companies get caught by a ransomware attack.
“Good specialist negotiators are very cost-effective, can provide intelligence on the ransomware group or affiliates, can advise if, by how much and over how long the negotiators might realistically negotiate down ransom demands for that specific group, and can effectively negotiate ‘proofs of life’ (of the stolen data) and extensions of time.
“These factors can help the victim decide if a negotiation could meaningfully reduce a ransom or provide a window to investigate and implement a response strategy, including notifying data subjects and regulators before a public leak of any stolen information,” Crompton said.
He also explained that “threat actors” (groups or individuals responsible for cyberattacks) are often just looking for a “pay day,” even if it is much lower than the initial demanded ransom. There is often room for a strong negotiation. Threat actors are often happy to receive a small proportion of the initial demand, but they have limits.
Bizarrely, some are even happy, after receiving payment, to explain how they breached the victim’s systems in the first place, giving insights on ways to avoid compromise in the future. There seems to be a tiny bit of honour among cyber thieves.
“However, the victim should be ready for a roller-coaster ride of threats to leak the data and should be ready to move quickly on the payment, once a deal has been reached,” Crompton said.
Is it Legal to Pay Ransom?
Even with a strategy and willingness to pay a ransom, in some jurisdictions it may not even be legal to pay cyber criminals to release a firm’s data. It is important to always check the local laws, said Crompton.
While ransomware attacks are international, multi-jurisdictional and often jurisdiction agnostic, there is no overarching international legal framework for cybersecurity, data protection or ransom payments.
In Hong Kong, Singapore and other Common Law countries, companies generally need to consider if the payment itself is illegal – this is generally a ‘proceeds of crime’ question. Such laws will rarely (if ever) have been tested for ransomware payments, but guidance is available from normal ransom cases.
It is also worth considering if the ransom payment will be made to a prohibited person – this is generally an AML/CTF/sanctions issue. Cyberattackers are, by nature, anonymous but a victim company must do due diligence, checking the information it has about the attackers against the latest sanctions lists.
Some jurisdictions will provide victims with a defense if the paying company notifies law enforcement before or immediately after making a ransom payment.
“Getting early advice is key if the company thinks it might have to pay a ransom. Some insurers have established checklists for if a ransom payment is covered under the policy. Again, it is best to check with the insurer as soon as the company thinks it might make a claim for a ransom payment under its policy,” Crompton said.
He added that data laws are getting more stringent and more localized. When the Europe-based general data protection regulation (GDPR) came into force in 2018, it was described as a “monster” and has had enormous implications across the world for how companies should store and process personal data.
The upcoming Chinese Personal Information Protection Law also poses a huge challenge for handling data. Laws are moving fast so companies need to move faster.
Compounding this problem, legal costs in the post-Covid-19 business atmosphere (just like any other costs) are being scrutinized and it can be a challenge to come up with the resources to stay on top of the game.
“The APAC cybersecurity and data privacy landscape is always evolving. And regulators understand that cyberattacks cannot always be prevented,” said Crompton.
“But they are looking for evidence that a victim company did all it could to protect the data, prepare for a breach and respond quickly. A good, well-executed incident response plan can even result in a regulatory warning instead of a financial penalty, helping both the company’s reputation and its bottom line.”
Five Things In-House Lawyers Can Do to Prepare for Cyberattacks
1. Connect
The complexity of the modern company means computer systems are likely “siloed” (stored in different locations). While this can be a great defense against cyberattacks, it also can be a vulnerability if in-house counsel can’t see the whole landscape of a company’s information assets.
Staying connected also means ensuring the C-suite, the board, HR and even external lawyers and cybersecurity professionals can all talk to each other should a cyber incident occur. On top of that, it is essential for general counsel to build a strong partnership with the chief information security officer (CISO).
2. Plan
CSO’s Global Intelligence Report: The State of Cybersecurity 2021 found only half of respondents said mandatory IT security training had been in place “for some time,” with 20% saying such initiatives were only just introduced “recently.”
This is too slow, the report said. Companies should be proactively planning for a cyber breach – since it is not a matter of ‘if,’ but ‘when.’ Regular, mandatory cybersecurity training can also be a key factor in a regulator’s decision whether to impose a penalty or not.
In developing a strategy, in-house counsel must start with the low-hanging fruit. Gaps in security often are the result of oversight or the accumulation of “exceptions” to security policies that build up over time. These are often the easiest parts to fix first.
3. Practice
“Practice as you want to play” is great advice for cybersecurity. An incident response (IR) plan can be tailored to a specific company, but if such a plan is immediately shoved into a filing cabinet it will be worse than useless – everyone will develop a dangerous false sense of security.
Instead, regularly conduct tabletop crisis exercises with all team members and have external experts “on call.” This includes walking a CEO through a communications strategy and practicing various responses with them. If the teams are walking away from these exercises without identifying weaknesses or asking questions, it’s likely there are still gaps in the plan.
4. Protect
The first responsibility for general counsel is to maintain attorney-client privilege before and after a breach. The aim of coordinating communications is about containing financial, market, technical, operational and reputational damage to limit the company’s potential legal liability.
There is no guaranteed way to maintain privilege when working with outside counsel, but it should be a top priority and general counsel is best-placed to advise on this.
5. Consider
Part of any good IR plan is to consider getting cyber insurance. A Cyber Insurance Risk Assessment is a quick, high-level analysis of a company’s risk level based on its technology, processes and people.
While cyber insurance can offload some risk, it doesn’t nullify all risks. For example, insurance cannot repair any damage to a company’s brand or core business. Insurance is helpful, but prevention will always be key.
Disclaimer: All views are personal and do not reflect that of the organization. The views shared are not intended for any legal advice and are for general information and education purposes only.
Featuring Jonathan Crompton
|
Jonathan Crompton is a partner in RPC’s Hong Kong office. |

Reynolds Porter Chamberlain LLP
rpc.co.uk
38/F One Taikoo Place 979 King’s Road Quarry Bay, Hong Kong
* This article was first published in the October 2021 issue of the IHC Magazine. You can read/download the magazine here.



 Jonathan Crompton
Jonathan Crompton