Thailand did not have a specific data protection law until 2019 when the Personal Data Protection Act (PDPA) and the Cybersecurity Act (CSA) were promulgated.
The PDPA sets high standards for personal data protections and is largely based on the EU’s General Data Protection Regulation (GDPR) with the intention of having equitable standards. For example, the PDPA mirrors the GDPR’s legal basis for data processing, extraterritorial applicability, and a data subject’s rights. However, the two are not identical.
While the PDPA specifically prescribes that a request for consent must be explicit in a written statement or via electronic means (unless such a request cannot be done), the GDPR focuses on consent being given by a clear affirmative act, such as an explicit oral statement. Also, the PDPA imposes criminal penalties for non-compliance in addition to monetary and administrative penalties.
2. The PDPA
The PDPA has been effective since 28 May, 2019, but the enforcement of most provisions is delayed until 2022. Key provisions for personal data protection, a data subject’s rights, duties of a data controller and processor, complaints, civil liabilities and penalties will not be effective until 1 June, 2022.
Scope of law
Generally, the PDPA applies to the collection, use or disclosure of personal data by a data controller or processor in Thailand. As in Article 3 of the GDPR, the PDPA also applies extraterritorially to the collection, use or disclosure of personal data of Thailand-based data subjects by a foreign data controller or processor in relation to the following activities:
- the offering of goods or services to data subjects in Thailand
- the monitoring of the behavior of data subjects taking place in Thailand
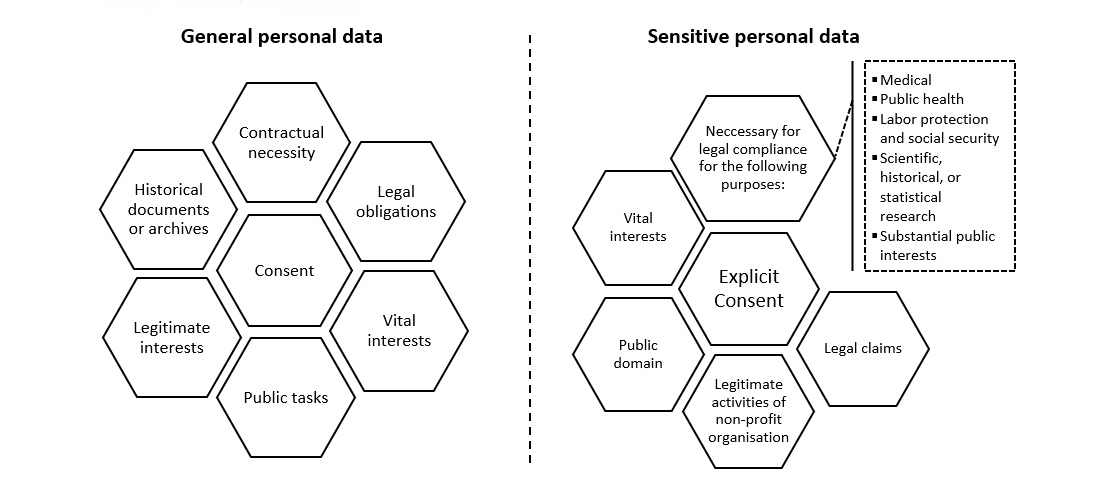
Definition of personal data
| Terms | Definitions under the PDPA |
| Personal data | Personal data Any information relating to a natural person, enabling the identification of a person, directly or indirectly, but not including the information of deceased persons. |
| Sensitive personal data | Sensitive personal data The law does not provide a definition. However, explicit consent is necessary for collecting personal data pertaining to:
The processing of sensitive data is subject to more stringent requirements and violations carry criminal penalties. |
Legal basis for processing personal data
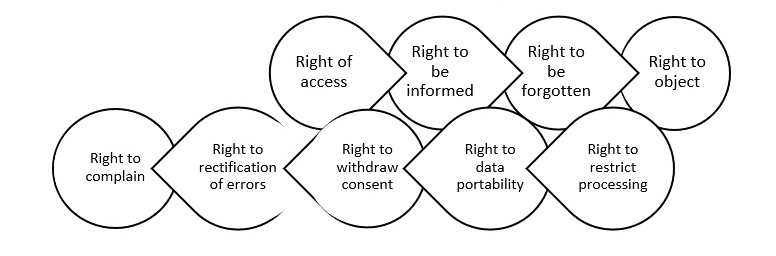
Rights of data subject
Under the PDPA, data subjects have the following rights regarding their personal data:
Duties of a data controller/data processor/data protection officer (DPO)
| Roles | Definitions | Duties |
| Data controller | A person or a juristic person with the power and duties to make decisions regarding the collection, use or disclosure of personal data | • Adopt appropriate technical and organizational measures to assure the collection, use and disclosure of personal data accords with the PDPA. For example: – Inform data subjects with sufficient information such as the purpose of data processing, data subject rights, etc; – Maintain and record processing activities; – Process data in accordance with the informed purposes; – Provide sufficient security measures to safeguard personal data. |
| Data processor | A person or a juristic person operating in relation to the collection, use, or disclosure of personal data pursuant to the orders given by or on behalf of a data controller, whereby such a person is not the data controller | • Provide sufficient guarantees for the technical and organizational measures required by the PDPA. For example: – Carry out processing activities pursuant to the lawful instructions given by the data controller; – Provide sufficient security measures to safeguard personal data; – Maintain and record processing activities. |
| Data Protection Officer DPO | Not specifically defined
Note: The Personal Data Protection Commission (PDPC) may prescribe the qualifications of the DPO in the future |
• Advise data controllers or data processors regarding compliance with the PDPA; • Investigate the collection, use or disclosure of personal data by data controllers or processors; • Liaise with the PDPC on data protection matters; • Keep personal data known or acquired confidential. |
Data breach
The data controller must notify the PDPC of any personal data breach without delay and, where feasible, within 72 hours after becoming aware of a breach, unless the data breach is unlikely to be a risk to the rights and freedoms of data subjects.
If a personal data breach is a high risk, the data controller must also notify the data subjects without delay after learning about the personal data breach and about the remedial measures being implemented.
Penalties
| Civil liability | Criminal penalties |
| A court may impose compensation as punitive damages up to double the actual damages | Imprisonment for a term not exceeding one year and/or a fine not exceeding Ƀ1 million, depending on the non-compliance |
Development of PDPA since enactment
Although the PDPA is already in force, the PDPC has not officially been set up and the subordinate laws under the PDPA are being drafted. Additionally, the regulating authority is preparing PDPA guidelines for seven sectors: 1) tourism, 2) public health, 3) education, 4) retail and e-commerce, 5) transportation and logistics, 6) real estate and 7) state operations.
3. The Cybersecurity Act
The CSA came into force on 28 May, 2019. The CSA aims to govern cybersecurity activities to prevent and combat cyberthreats.
A “cyberthreat” is broadly defined as “any action or unlawful undertaking done using a computer, computer system or undesirable program with an intention to cause harm to a computer system, computer data or other relevant data, and includes imminent threats that would cause damage or affect the operation of a computer, computer system, or other relevant data.”
Under the CSA, cyberthreats can be categorized into three levels of severity:
- non-critical cyberthreats
- critical cyberthreats
- crisis cyberthreats
Each threat level depends on the effect to a country’s infrastructure, national security, economy, public health, public order or important information infrastructure. The level of threat determines the level of response the Cybersecurity Supervision Committee (CSSC), the authority tasked with monitoring and supervising compliance with the CSA, must use to combat such threat.
For example, in a serious cyberthreat specific provisions authorize the CSSC to examine computers, computer systems and data and seize computers, computer systems or any other equipment as necessary.
Critical Information Infrastructure
The CSA defines Critical Information Infrastructure (CII) as a computer or computer system used by a government agency or private organization that relates to maintaining national security, public security, national economic security or public interest infrastructures.
The CSA also designates certain organizations as Critical Information Infrastructure Organizations (CIIO), including organizations providing: 1) national security, 2) important public services, 3) banking and finance, 4) information technology and telecommunications, 5) transportation and logistics, 6) energy and public utilities, 7) public health and 8) other services prescribed by the National Cybersecurity Committee (NCSC). Therefore, a private sector operator providing any of these services is regarded as a CIIO and is subject to the CSA.
Policies and Plans
The NCSC is developing a master plan and subordinate regulations related to cybersecurity in Thailand. Recently, the NCSC approved subordinate regulations including: 1) policies and plans in relation to cybersecurity; 2) a code of practice and a standard framework regarding cybersecurity for government agencies and the CIIO; 3) NCSC’s notification relating to the establishment, duties and authorities of the national coordinating agencies for the security of computer systems; 4) the NCSC’s notification in relation to the duties and responsibilities of the coordinating agencies for the security of computer systems for the CIIO; and 5) the NCSC’s notification prescribing characteristics of the organizations with a mission or that provide services as a CIIO. However, these provisions are in the early stages of development and will require further approval.
Coping with Cyberthreats
To cope with cyberthreats, the CIIO has the following duties: 1) notify the contact information of the owner, person in possession of and operator of a computer system, along with any changes thereto to the authorities; 2) comply with the code of practice and minimum cybersecurity standards; 3) conduct risk evaluations of cybersecurity at least once per year and submit the results to the authorities; 4) implement mechanisms or procedures to monitor and resolve any cyberthreats or incidents relating to the CIIO; and 5) report any cyberthreats.
While the CSA requires the CIIO to ensure that appropriate cybersecurity measures are in place to protect its organizations from cyberattacks, the PDPA also requires organizations to ensure that both technical and organizational security measures are implemented to prevent unauthorized or unlawful loss, access to, use, alteration, correction or disclosure of personal data.
4. Self-Check
Is your entity ready for the full enforcement of PDPA?
Given the grace period until June 2022, it is crucial that organizations review their personal data related activities to ensure their compliance with the PDPA.
| Steps | Self-check | Steps | Self-check |
| Data mapping | ✓ | Consent management | ✓ |
| DPO appointment | ✓ | Security measure | ✓ |
| Training/Awareness | ✓ | Data subject rights management | ✓ |
| Record of data processing activity | ✓ | Data processing agreement | ✓ |
| Privacy notice | ✓ | Data breach management plan | ✓ |
How to effectively handle data breaches?
Data breaches may occur for a variety of reasons. Therefore, organizations should create measures to monitor and take pre-emptive actions when handling any data breaches. A data breach management plan should be adopted to enable organizations to manage data breaches effectively and systematically. Moreover, regular training teaching personnel about personal data protection is recommended.
5. Conclusion
As digital business rapidly expand, the PDPA and the CSA provide an important foundation for organizations to handle and deal with potential legal exposures and risks regarding breaches to personal data and cyberthreats.
While some organizations may choose to wait for the full implementation and subordinate regulations under the PDPA, early actions in complying with these laws should be considered to grasp the benefits (and avoid punishment) of technology advancements. Operators in Thailand should undertake internal organizational preparations to comply with the PDPA, as implementation of required measures may take several months.
Disclaimer: All views are personal and do not reflect that of the organization. The views shared are not intended for any legal advice and are for general information and education purposes only.
By Arkrapol Pichedvanichok and Visitsak Arunsuratpakdee
 Arkrapol Pichedvanichok Arkrapol Pichedvanichok
Arkrapol is a Senior Partner and head of the corporate |
 Visitsak Arunsuratpakdee Visitsak Arunsuratpakdee
Visitsak is a Partner at Chandler MHM specializing in |
![]()
Chandler MHM Limited
chandlermhm.com
17th and 36th Floors, Sathorn Square Office Tower
98 North Sathorn Road, Silom, Bangrak
Bangkok 10500, Thailand
* This article was first published in the October 2021 issue of the IHC Magazine. You can read/download the magazine here.


